

February 12th, 2019
2 min read

A newer addition to the ERP Suites Clarity system monitoring tool, Security Management presents all your JD Edwards security information in one convenient dashboard. Why is this a big deal? Imagine an auditor is accessing the security of your JDE EnterpriseOne (E1) system. With Security Management, you can provide the information they need at a glance. Look no further than the Security Summary section to check metrics including:
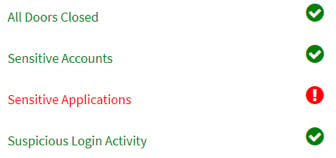
The Security Summary section also allows you to quickly see if your company is an All Doors Opened/Closed security framework. It indicates if any sensitive accounts are compromised and if suspicious login activity has occurred.
In the example below, we see a customer with 735 users enabled and 1,130 users disabled. They might ask themselves, “Should we have this many users enabled at this time?”, or “Do I really have this many active users on the system?” By clicking on the “Enabled” or “Disabled” boxes, they can see which users are enabled or disabled without logging in to E1 and filtering on the security table. The little red boxes tell them a recent user has been removed from the enabled list and added to the disabled list. Notice 7% of the overall security has been defined at the user level. Since this is not always the best security framework, the customer can now focus their efforts on discovering why security was defined this way rather than by *PUBLIC or Role. 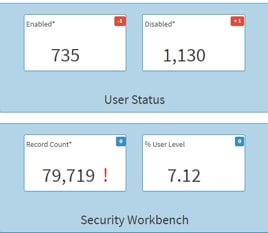
Password Exceptions tracks the number of users in the system who do not require a password change. Click on the box to review which IDs have exceptions and pinpoint users you need to remove from the list.

Invalid Attempts tallies users who have unsuccessfully attempted to log in. Again, you can click on the box to scan the user list and determine whether or not they were disabled in the process. Quickly spot excessive failed login attempts and then check the user in question. This feature can help you uncover suspicious activity that might be occurring as well.
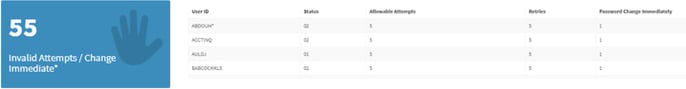
Roles w/o Environments shows how many roles in the system don’t have any environments assigned. Drill into the detailed list to figure out which ones are needed and which are not so you can clear out the excess. If you have an issue with new role set up and a user can’t log in, Roles w/o Environments is an excellent place to start.

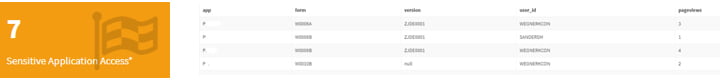
Sensitive Application Access box displays the number of applications deemed sensitive in your E1 system. This is extremely important data to your JDE security. Click for an in-depth look at the applications and the users accessing them.
Rounding out the Security Summary section is a snapshot of the company security model. Are all doors closed? Are there any security issues with sensitive accounts or applications? Is there suspicious login activity? Clarity will alert you to trouble with a red exclamation point. And you can hover over the list for details.
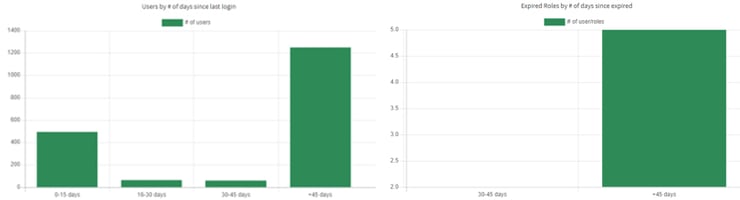
The Aging Report section provides important inactivity data such as Users by number of days since last login and Expired Roles by number of days since expired. Use this information to clean up your JDE security system. Clarity gives you a heads up — users may be disabled if they haven’t logged in for 45 days or more and if their roles have expired.
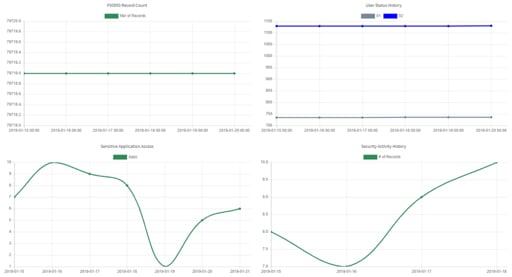
Last but certainly not least, Security Management offers a Historical Utilization section. As we found in the Application Management blog, these graphs can pull data from yesterday, last week, or even the entire month. Set a custom range if you want to. You’ll find vital security change data, including:
Don’t spend countless hours searching for security specifics. Let ERP Suites Clarity do it for you. Maximize these features to provide greater reassurances to your company.
New to ERP Suites Clarity and want to learn more? Contact us. We’re happy to show you around.
Miranda Cluxton & Frank Jordan
Miranda Cluxton began her career as a co-op with ERP Suites nearly ten years ago and quickly rose to a leading CNC. She is a Clarity product champion using data analysis to inform better decision making around user performance and security. Her insights into the customer experience continue to shape our products and processes. Frank Jordan is a CNC technology consultant with over 300 customer engagements. His work with JD Edwards Orchestrator Studio earned ERP Suites three Distinguished Partner Awards for digital innovation at INFOCUS 18. Frank is the co-author of Advanced Tuning for JD Edwards EnterpriseOne Implementations and a frequent conference presenter.