
JD Edwards has powerful native security capabilities available to users, but it takes expertise and experience to optimally leverage these capabilities against the increasing sophistication of cyber criminals. The following article discusses the JD Edwards security best practices we recommend to our customers regarding user roles.
Open-Security Models versus Closed-Security Models
JD Edwards is delivered to customers with an open security model, meaning all users have access to everything in the system. In an open or partially open JD Edwards security model, most if not all of a company’s users have the equivalent of administrator accounts (for instance, they may be logging in with the JDE account itself). This effectively gives them unfettered access to the system, and along with it the ability to manipulate data and initiate processes at will. This is a recipe for problems on any number of levels. For instance, if hackers are able to hijack one or more user accounts, they could potentially use them to access sensitive data or direct payments to themselves (either by setting up a new vendor or changing the routing and account information for an existing vendor). An employee could also take advantage of an open security scenario to carry on the same sort of activities, but with potentially even greater odds for success given that they’re working on the inside and have the ability to hide suspicious transactions.
In addition to potentially fraudulent activity, open systems are also vulnerable to unintentional mishaps. For instance, if Becky is out of the office one day, John may try to do something she would normally handle, only to inadvertently cause harm because he lacks Becky’s expertise and/or familiarity with a particular situation.
In light of such considerations, it’s essential that companies running JD Edwards adopt a closed-security model. Closed models utilize an all-doors closed approach along with well-defined user roles based on distinct business processes, thereby limiting who has access to what.
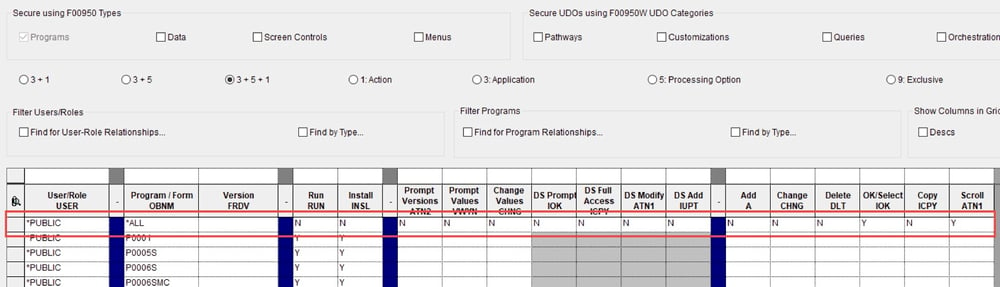
No user can access any kind of data or perform any type of operation that has not been explicitly granted to him or her. The closed-security approach could also be thought of as a ‘zero-trust policy,’ and falls under a general ‘segregation of duties’ business philosophy, which offers benefits extending well beyond security concerns.
Role-Level Security versus User-Level Security
Security within JD Edwards can be set according to roles or else made user-specific. ERP Suites strongly recommends role-based security as opposed to user-level security. Roles should be created to cover all necessary functions—for example, Journal Entry or Receiving. Roles should have the required level of detail (access to Form and Row exit programs and called UBEs) so all steps necessary to complete the process are included. Ideally, all user processes should have corresponding roles. Access to business processes is controlled by adding or removing the appropriate roles for users. If changes to business processes ever need to be applied, you need only modify the appropriate roles rather than having to individually modify every user who falls under those roles. Users will only be able to interact with the level of functionality you set for them. You can even limit what users are able to see on a given screen, which can aid with both training and efficiency given that users will not have to view or interact with any functionality other than what they need to perform their assigned tasks. This gives the user a streamlined view of their responsibilities.
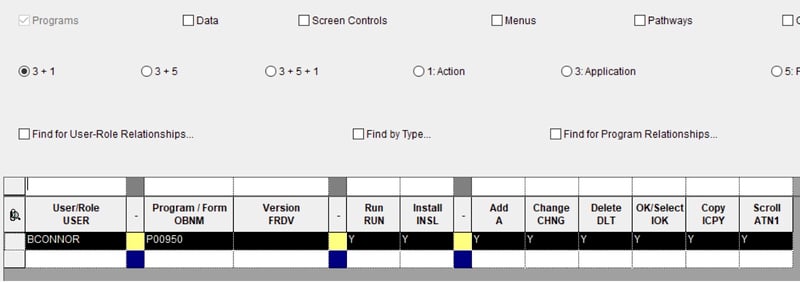
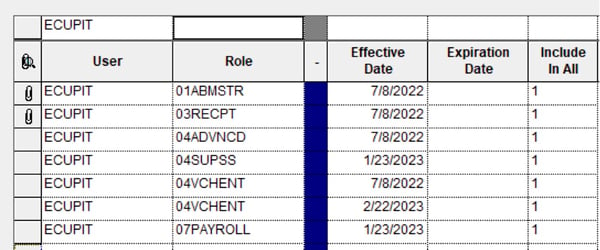
While this approach offers great potential benefits in terms of both security and efficiency, it’s essential to review user roles thoroughly in order to ensure that the security settings for a given role correspond to job-duty expectations. For example, you may encounter situations where users have the ability to enter a purchase order but cannot actually perform a search and select items because that functionality falls under a different role. This consideration hearkens back to the necessity for expertise and experience in JD Edwards security, as trained, experienced personnel will understand the process trees affected by even seemingly minor changes.
Segregating Program and Data Access
When setting up user roles, we recommend segregating program access from data access. This is especially important with regard to accounts payable security, as you don’t want one user having unfettered access to set up vendors, alter existing vendors, and authorize payments at will. Again, it’s essential to create roles for each aspect of a given process. This strategy protects both your company and your employees as it adds multiple layers to your security architecture and creates clear user activity records for auditing purposes.
It’s also important to carefully restrict access to your production environment. There is almost no reason for CNCs or developers to have wide-open sysadmin access to production, as virtually anything they need to do can be done from a lower environment and rolled out into production by appropriate support staff once a change has been authorized. Full access to Production should be temporary, authorized, and logged.
Internal Auditing and Due Diligence
While it’s a good idea to bring on independent auditors from time to time, there is no substitute for continual, internal vigilance. You know your personnel and processes better than anyone else. We encourage you to segregate duties, set up an accountability hierarchy (including an authorization process, such as for payments over a certain dollar amount), and organize a program for regularly auditing the system. Familiarize yourself with common fraud indicators, and be on the lookout for issues that often tend to slip between the cracks, such as removing terminated employees' accounts from the system.
Get A Customized Security Assessment
ERP Suites offers a customized security assessment for your business. We’ll review your current security configuration and make recommendations on how you can improve. Schedule a Free 1-on-1 with our JDE security expert today for more information.
Topics:



.png?width=650&height=325&name=Blog%20Images%202_1%20(4).png)
.png?width=650&height=325&name=Blog%20Images%202_1%20(5).png)
.png?width=650&height=325&name=Blog%20Images%202_1%20(3).png)
.png?width=650&height=325&name=Blog%20Images%202_1%20(2).png)
.png?width=650&height=325&name=Blog%20Images%202_1%20(1).png)
.png?width=960&height=540&name=Blog%20Images%20(96).png)

.png?width=960&height=540&name=Blog%20Images%20(90).png)
.png?width=960&height=540&name=Blog%20Images%20(88).png)
.png?width=960&height=540&name=Blog%20Images%20(87).png)
.png?width=960&height=540&name=Blog%20Images%20(86).png)
.png?width=960&height=540&name=Blog%20Images%20(85).png)
.png?width=960&height=540&name=Blog%20Images%20(83).png)
.png?width=960&height=540&name=Blog%20Images%20(82).png)