
Imagine that you’re busily working at your desk one day when your laptop screen suddenly goes dark and the following message appears:
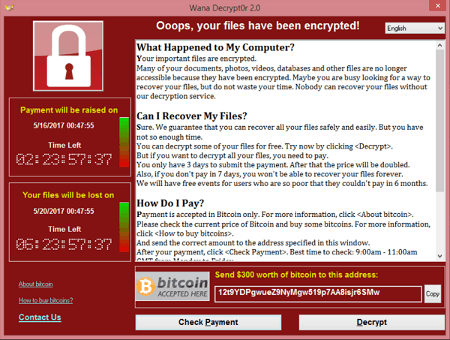
This is a ransomware attack. Your data is now encrypted and inaccessible. Your business is at a complete standstill. Everything you’ve worked so hard to build is being held hostage by cyber criminals, and the clock is ticking. If you don’t pay within three days, their ransom demand will increase—who knows by how much. If you still don’t pay after a week, you may lose all of your data forever. You’ve heard about this sort of thing, but you never imagined it could happen to you. Your mind races with questions: Who did this? How did they access my systems? Why didn’t our security software prevent this? And most importantly…What are the steps to take after ransomware?
How Does Ransomware Attack
When it comes to ransomware, communication is the name of the game. Once ransomware gains access to your network, it will spread like wildfire, gradually infecting everything. Yet, there is usually a method to the madness. Just as in warfare, where any competent attacking force will seek to neutralize its opponent’s defenses and command-and-control hubs at the outset of a conflict, cyber criminals design ransomware to disable your security apparatus and turn your own network against you. The following systems are likely to be targeted first:
-
Antivirus/Anti-malware Software: Cyber criminals know that companies rely upon these applications for their frontline defense against malicious software. For this reason, they will often program ransomware to disable and/or uninstall them when an attack begins.
-
Backup Solutions: Most companies that are hit by ransomware attacks will automatically try restoring from their last clean backups. If successful, they can regain access to their systems and simultaneously purge the ransomware infection. For this reason, intelligent cyber criminals design ransomware to identify and target backup solutions early in the infection process, hoping to remove this option and leave the victim with no choice but to pay the ransom demand.
-
Databases and Large Transactional Systems: Think communication hubs and command-and-control nodes here. Because they store, process, and route data your entire business infrastructure depends upon, databases and large transactional systems give ransomware the greatest chance of spreading throughout your organization.
Potential Signs of a Ransomware Attack
As per the image at the top of this article, ransomware will often identify itself because the cyber criminals who infected you will expect you to pay them for the encryption keys needed to unlock your data. In this case, obviously, you’ll know what’s going on right away. If you know what to look for, however, you may be able to thwart an attack before it gets this far. In 2021, 39% of businesses struck by ransomware attacks were able to successfully stop the encryption process. This was up from 24% in 2020—a considerable improvement. Vigilance pays big dividends.
Here are a few common ransomware indicators that should prompt you to investigate:
- Unusual CPU Activity: Ransomware will try to encrypt your entire system. This is a lengthy and resource-intensive process. For this reason, unusually high and/or sustained CPU utilization on machines that are not usually very active could indicate an infection.
- Recently Installed Files: Sophisticated antivirus and anti-malware software may flag suspicious files that have been recently installed. At times, they may also act to interdict potentially malicious software before it can make changes to your system.
- Antivirus/Anti-malware Failure: Because ransomware often tries to disable your security software at the start of an attack, you may see security warnings pop up indicating that your antivirus/anti-malware services have stopped unexpectedly.
- DNS Protection Software: DNS (Domain Name System) protection software operates by monitoring traffic between URLs and IP addresses and blocking traffic that is either suspicious or has been blacklisted. Malicious types of software like ransomware will often try to redirect traffic or even hijack a trusted location and use it against you. DNS protection software will alert you to suspicious activity and work to block it within defined parameters.
For more detailed information on known types of ransomware and other potential infection indicators, please visit CISA.gov and stopransomware.gov.
First Steps after a Ransomware Attack
Having a ransomware response plan is very important to the continued success and reputation of your business. The recommended steps to take after a ransomware attack are outlined below so you know how to deal with ransomware if it ever strikes your business.
Stop the Spread
Because ransomware is dependent on network communications, the first thing you’ll want to do when you suspect you’re under attack is to disconnect all network connectivity—not just at the firewall level but internally as well. This will help limit the impact of the ransomware by impeding its ability to spread, using your own network infrastructure as a type of high-speed rail system. You’ll then want to shut down all of the individual machines that were connected to the network, as this will interrupt the encryption process on any of the machines that were infected. Any machines that have been recently connected to the network should be considered infected and shut down until you’ve learned more about the type of ransomware infecting your systems.
With your network down, you’ll need an alternative means of communicating with your personnel. Online communications platforms like Zoom, WebEx, and Microsoft Teams are useful for this purpose, especially given that they can be accessed from tablets and smartphones.
Begin Forensic Analysis
Once your network connections have been disabled, you’ll want to selectively bring up machines until you find one that is infected. Be sure to scan your event and security logs on infected machines, as this will help you identify the date and time of the initial infection.
Decrypting Ransomware
If you report the attack to the FBI, they could provide information that might prove helpful, and may even be able to assist with recovering your data if the infection is a type of ransomware they’ve dealt with before. There are also a variety of free, reputable online tools for identifying and unencrypting ransomware. You should be aware that trying to find or else develop the right keys to unencrypt ransomware can take time—perhaps more time than you have before the ransomware deletes your data or your business suffers devastating financial harm from extended downtime. Unfortunately, decryption tools will sometimes inadvertently corrupt your data in the process of unlocking it, so you may have to try more than one, and it would be a good idea to back up all of your infected systems prior to trying one of these tools. You should also note that decrypting ransomware is not the same thing as removing it from your system. The decryption process merely restores access to your data. The malicious software still needs to be quarantined or removed from your machines, or else you run the risk of further problems, such as data theft.
Incredibly enough, ransomware has become something of a perverse business, and like any other type of business endeavor the developers of ransomware are always trying to improve their ‘product.’ Intelligent cyber criminals practice the "Know Your Enemy" doctrine. They have access to all of the same publicly available anti-ransomware tools that the rest of us do, and they follow developments in the cybersecurity industry closely. You can be sure they’re doing their best to make it as difficult and time-consuming as possible to thwart them. Their aim is to drive you to desperation.
Restoring from Backup
After suffering a ransomware attack, most businesses will automatically work to restore their systems from backup, and will often rebuild infected machines entirely. The most important aspect of initiating a restore from backup is to accurately pinpoint the time of the initial infection, otherwise when you restore your systems, you may end up restoring the ransomware right along with everything else. As noted previously, once you’ve completed the restore process, you may also want to follow up by completely rebuilding the infected machines. You’ll also want to be sure that you have all of the most recent software patches in place, as ransomware often exploits defects in older software releases.
It’s important to remember that ransomware will often seek to corrupt your backup solution at the beginning of the infection process, so as to neutralize the restore option and prompt you to pay the ransom. For this reason, your backup solution should be kept separate from the rest of your network and should be incorruptible. Air-Gapped backup solutions, such as ERP Suites CyberRecovery, are ideal for this purpose because they fulfill both requirements.
Whatever backup/restore solution you ultimately choose, it should be thoroughly tested for reliability. There’s nothing so devastating as discovering too late that you can’t restore because of a problem that might have been identified and remedied long ago with some simple testing! You’ll also want to test your backup/restore solution so that you’ll have a clear understanding of what the restore process involves and how long it will take.
Planning for Ransomware Attacks
There are many different types of ransomware, with new variations appearing all the time; but the good news here is that they all operate in roughly the same manner. For this reason, it’s possible to develop effective ransomware response plans that can be implemented quickly. An effective ransomware response plan will do five things:
- Identify the personnel designated to lead the response effort and outline how they are to communicate and coordinate their efforts. Working with a managed security services partner will make this process much smoother.
- Prescribe the quickest and safest way to shut the network down so as to limit the spread of the infection. It’s important that this be determined in advance so that time is not wasted researching and/or debating the matter once an attack is underway.
- Outline how forensic testing will be implemented to determine the exact nature of the infection (once the spread has been halted) and how it gained access to the system.
- Provide guidelines on attack reporting (customers, law enforcement, and so forth) and, based on the particular type of ransomware involved, steps for determining and implementing the appropriate response (decryption, restore from backup, etc).
- Outline steps for bringing the network back online, testing to ensure functionality, ensuring that the ransomware has been completely removed, and safeguarding against future attacks (once it’s understood how the attack came about).
Ideally, your response plan should be designed to serve as a general framework, allowing enough flexibility for your response team members to adapt it to the specific ransomware variant you’re dealing with. Having a flexible plan in place before an attack happens will allow you to meet the threat with as little hesitation, uncertainty, and debate as possible. This could potentially save you a great deal of time, money, and frustration.
To Pay or Not to Pay…
In 2021, 32% of ransomware victims paid the ransom demand in an effort to recover their data. This was up 6% from 2020. Given the expense and downtime involved with recovery and decryption efforts, paying the ransom may be tempting, but there are some caveats you should be aware of before you take this option.
First of all, you’re probably wondering: “If I fork over the cash, will they really give me the keys?” You may be surprised to learn that, yes, more than likely, they will. As mentioned previously, ransomware has become a business of sorts. Cyber criminals are now selling ransomware code to other criminals who want to launch their own attacks. For this reason, the most popular ransomware will almost always provide a proper unlock code. Paying the ransom is like leaving a positive review for a product: you’re giving a testimonial that the ransomware works. If cyber criminals never gave their victims the decryption keys, there would be no reason for anyone to pay and thus no money to be made in this sort of criminal enterprise. That said, as mentioned previously, decrypting the ransomware does not remove it from your system. It will still need to be quarantined or, better yet, removed altogether so that it doesn’t pose a continuing threat.
Of course, paying the ransom publicly advertises that you were unable to breach the code. This bolsters the confidence of anyone who might be interested in using the same ransomware against someone else. It may also embolden other cyber criminals to try their luck attacking you with other forms of ransomware. After all, if you paid before, you might just pay again. For this reason, the FBI discourages companies from paying ransomware demands.
When considering whether you should pay a ransom demand, you will also want to note that, in 2021, most businesses that chose to pay the ransom were only able to recover about 65% of their data. A mere 8% of those who paid the ransoms were able to recover everything. So, even if you pay, the odds are that you’re unlikely to recover all of your data. For this reason, you’ll need to factor the expense of permanently losing significant quantities of data against the costs involved with a restore-from-backup process—assuming the ransomware hasn’t infected your backups as well.
There may also be important legal ramifications involved with paying a ransomware demand. For instance, if the ransomware attack originates from a country considered hostile and/or subject to economic sanctions—such as Russia or Iran—it would be a serious crime for you to transfer funds to them. For this reason, you’ll want to be sure you’re on safe legal ground before proceeding with any kind of payment.
Reporting an Attack
Because ransomware attacks cross state lines—and sometimes international borders as well—they fall under federal jurisdiction, and federal agencies will want you to report any such incidents. State agencies may want you to do this as well. This not only helps law enforcement agencies track criminal activity and potentially trace it back to its source, it also helps them develop decryption keys to help others who come under attack in the future.
Legally, you may find that you have no choice but to report a ransomware attack—to your customers as well as to the appropriate law enforcement agencies. Failure to do so could invite serious legal action against your company. Furthermore, there is also a risk that your customers may decide to file suit against your company if they feel that you failed to properly safeguard their data.
For these reasons, you’ll want to explore the laws that apply to your situation—as well as your contractual obligations to your customers—to be sure that you’re in compliance on all fronts. These issues should also be addressed in your ransomware response plan so that your response team members understand your company’s obligations under the law and act accordingly.
Hopefully, you have taken the necessary security steps to secure your business data against a ransomware attack. This will give you the best chance of avoiding live ransomware response actions. However, all businesses should be aware of these steps and have a sound ransomware response plan.
Shawn Meade leads the Information Security team at ERP Suites. He has been in the IT industry for over 20 years and dealt with Information Security throughout his career including work with PCI, HIPPA, and HITRUST.
Topics:


.png?width=960&height=540&name=Blog%20Images%20(65).png)
.png?width=960&height=540&name=Blog%20Images%20(49).png)
.jpg?width=6000&height=4000&name=data%20center%20checklist%20(1).jpg)




